Difference between revisions of "SSH Tunnel Utility"
| (13 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
[[Category:Manager]] | [[Category:Manager]] | ||
[[File:Manager SSH Tunnel Utility Icon.png|class=appIcon]] | [[File:Manager SSH Tunnel Utility Icon.png|class=appIcon]] | ||
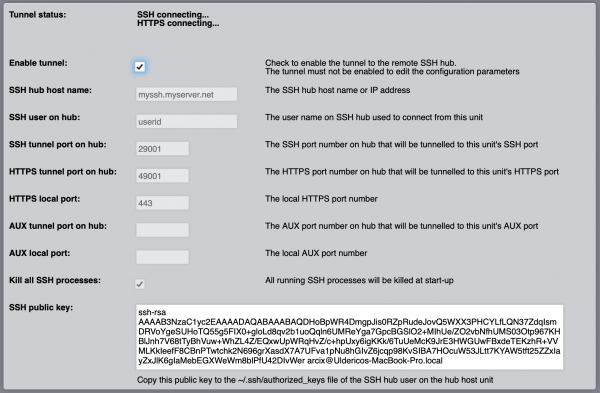
| − | The SSH Tunnel Utility | + | The SSH Tunnel Utility allows to create secure reverse SSH-based connection tunnels to a remote SSH server (hub). Up to three concurrent tunnels can be established, one for local SSH console access, one for the HTTPS Web server connections and one additional (AUX) tunnel to any local service network port like, for example, the Modbus TCP Gateway server. |
| − | + | [[File:SSHTunnelUtility1.png|border|600px|center|SSH Tunnel Utility]] | |
| + | |||
| + | |||
| + | A tunnel is configured by setting the local TCP port of a network server, and the remote TCP port for the tunnel on the remote SSH server. Connecting to the TCP port associated to a tunnel on the remote server will route the connection and all established traffic, through the tunnel, to the local TCP port defined in the tunnel configuration. | ||
| + | |||
| + | Thanks to the SSH tunnels, a local HSYCO Server that lacks inbound connectivity, could still be accessed via a remote and accessible SSH server configured as a tunnel end-point. | ||
| + | |||
| + | The tunnel configuration parameters can be modified only when tunneling is not enabled. | ||
| + | |||
| + | The "SSH hub host name" is the network name or IP address of the remote SSH tunnel server (hub). | ||
| + | |||
| + | In order to establish a secure connection, the SSH Tunnel Utility authenticates on the remote SSH tunnel server with the user id set in "SSH user on hub" and the "SSH public key" of the HSYCO Server, that must be copied into the "authorized_keys" file on the hub for that user. | ||
| − | + | If the SSH, HTTPS or AUX port number fields are left empty, the corresponding tunnel is not activated. | |
| − | + | {{note|Note that the tunnels are only active while HSYCO is running. Restarting HSYCO, all connections established through the tunnels, including the SSH connection, are dropped.}} | |
| − | |||
| + | == The configuration API == | ||
| − | + | The SSH Tunnel Utility can be dynamically configured, and the tunnel service enabled and disabled, with USER calls in ENVENTS and the user() command in Java or JavaScript. | |
| + | |||
| + | In the following EVENTS example, the tunnel is enabled at 08:00 and disabled at 18:00. | ||
| + | |||
| + | TIME 0800 : USER sshtunnel.enable = true | ||
| + | TIME 1800 : USER sshtunnel.enable = false | ||
| + | |||
| + | === User commands === | ||
| + | |||
| + | {| class="wikitable" | ||
| + | !ID | ||
| + | !Value | ||
| + | !Description | ||
| + | |||
| + | |- | ||
| + | |rowspan="2" |sshtunnel.enable | ||
| + | |true | ||
| + | |enable the tunnels | ||
| + | |- | ||
| + | |false | ||
| + | |disable the tunnels | ||
| + | |||
| + | |- | ||
| + | |sshtunnel.host | ||
| + | |<host> | ||
| + | |the SSH hub host name or IP address | ||
| + | |||
| + | |- | ||
| + | |sshtunnel.user | ||
| + | |<user> | ||
| + | |the user name on SSH hub used to connect from this unit | ||
| + | |- | ||
| + | |sshtunnel.ssh.port | ||
| + | |<port> | ||
| + | |the SSH port number on hub that will be tunnelled to this unit's SSH port | ||
| − | + | |- | |
| + | |sshtunnel.https.port | ||
| + | |<port> | ||
| + | |the HTTPS port number on hub that will be tunnelled to this unit's HTTPS port | ||
| − | + | |- | |
| + | |sshtunnel.https.local.port | ||
| + | |<port> | ||
| + | |the local HTTPS port number | ||
| − | + | |- | |
| + | |sshtunnel.aux.port | ||
| + | |<port> | ||
| + | |the AUX port number on hub that will be tunnelled to this unit's AUX port | ||
| − | + | |- | |
| + | |sshtunnel.aux.local.port | ||
| + | |<port> | ||
| + | |the local AUX port number | ||
| − | + | |- | |
| + | |rowspan="2" |sshtunnel.kill | ||
| + | |true | ||
| + | |all running SSH processes will be killed at start-up | ||
| + | |- | ||
| + | |false | ||
| + | |don't kill SSH processes at start-up | ||
| − | + | |} | |
| − | The | + | {{note|The tunnel utility must not be enabled to change the configuration parameters with API commands.}} |
Latest revision as of 18:19, 14 October 2020
![]() The SSH Tunnel Utility allows to create secure reverse SSH-based connection tunnels to a remote SSH server (hub). Up to three concurrent tunnels can be established, one for local SSH console access, one for the HTTPS Web server connections and one additional (AUX) tunnel to any local service network port like, for example, the Modbus TCP Gateway server.
The SSH Tunnel Utility allows to create secure reverse SSH-based connection tunnels to a remote SSH server (hub). Up to three concurrent tunnels can be established, one for local SSH console access, one for the HTTPS Web server connections and one additional (AUX) tunnel to any local service network port like, for example, the Modbus TCP Gateway server.
A tunnel is configured by setting the local TCP port of a network server, and the remote TCP port for the tunnel on the remote SSH server. Connecting to the TCP port associated to a tunnel on the remote server will route the connection and all established traffic, through the tunnel, to the local TCP port defined in the tunnel configuration.
Thanks to the SSH tunnels, a local HSYCO Server that lacks inbound connectivity, could still be accessed via a remote and accessible SSH server configured as a tunnel end-point.
The tunnel configuration parameters can be modified only when tunneling is not enabled.
The "SSH hub host name" is the network name or IP address of the remote SSH tunnel server (hub).
In order to establish a secure connection, the SSH Tunnel Utility authenticates on the remote SSH tunnel server with the user id set in "SSH user on hub" and the "SSH public key" of the HSYCO Server, that must be copied into the "authorized_keys" file on the hub for that user.
If the SSH, HTTPS or AUX port number fields are left empty, the corresponding tunnel is not activated.
The configuration API
The SSH Tunnel Utility can be dynamically configured, and the tunnel service enabled and disabled, with USER calls in ENVENTS and the user() command in Java or JavaScript.
In the following EVENTS example, the tunnel is enabled at 08:00 and disabled at 18:00.
TIME 0800 : USER sshtunnel.enable = true TIME 1800 : USER sshtunnel.enable = false
User commands
| ID | Value | Description |
|---|---|---|
| sshtunnel.enable | true | enable the tunnels |
| false | disable the tunnels | |
| sshtunnel.host | <host> | the SSH hub host name or IP address |
| sshtunnel.user | <user> | the user name on SSH hub used to connect from this unit |
| sshtunnel.ssh.port | <port> | the SSH port number on hub that will be tunnelled to this unit's SSH port |
| sshtunnel.https.port | <port> | the HTTPS port number on hub that will be tunnelled to this unit's HTTPS port |
| sshtunnel.https.local.port | <port> | the local HTTPS port number |
| sshtunnel.aux.port | <port> | the AUX port number on hub that will be tunnelled to this unit's AUX port |
| sshtunnel.aux.local.port | <port> | the local AUX port number |
| sshtunnel.kill | true | all running SSH processes will be killed at start-up |
| false | don't kill SSH processes at start-up |