Difference between revisions of "Protege"
| (43 intermediate revisions by the same user not shown) | |||
| Line 2: | Line 2: | ||
The integration with HSYCO can be accomplished with a TCP/IP network connection. | The integration with HSYCO can be accomplished with a TCP/IP network connection. | ||
| − | + | == Protege Configuration == | |
| + | |||
| + | ProtegeGXServer needs to be configured to accept a connection on a defined TCP/IP port with the ICT Automation and Control Service protocol. | ||
*A PIN must be set (4 to 6 digits) | *A PIN must be set (4 to 6 digits) | ||
| − | * | + | |
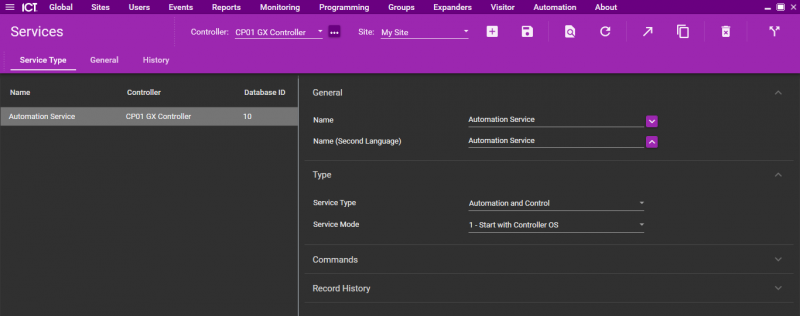
| − | * | + | Open Programming > Services |
| − | + | Select the controller associated to the Protege I/O Server | |
| − | + | Click "Add" to activate the "Automation and Control" service | |
| + | |||
| + | *Under "Service Type /General" specify a name (freely choose), for the main and the second language. | ||
| + | *Under "Service Type /Type" select "Automation and Control" then set "Service Mode" to "1 - Start with Controller OS" | ||
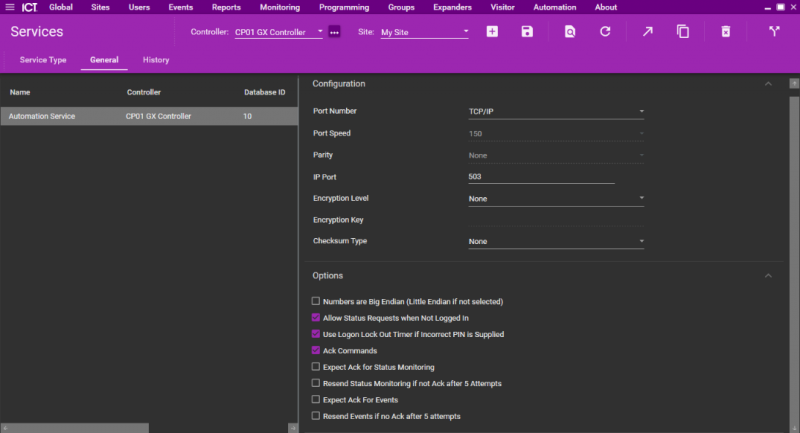
| + | *Under "General / Configuration" select "TCP/I" then specify a "Port Number". Set "Encryption Level" and "Checksum Type" to "None" | ||
| + | *Under "General / Options" enable "Allow Status Requests when not Logged In", "Use Logon Lock Out Timer if Incorrect PIN is Supplied", "Ack Command" | ||
| + | |||
| + | This driver works with Little Endian format | ||
| + | |||
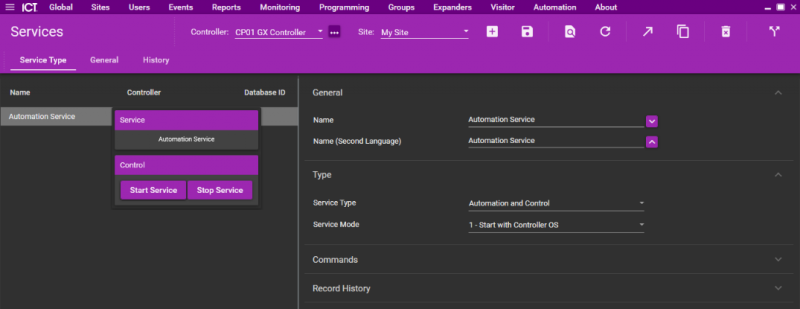
| + | Click "Save" to confirm. Right click on the service and select "Start Service" | ||
| + | |||
| + | [[File:protege01.png|800px]] | ||
| + | |||
| + | [[File:protege02.png|800px]] | ||
| + | |||
| + | [[File:protege03.png|800px]] | ||
| + | |||
[[Category:I/O Server]] | [[Category:I/O Server]] | ||
| Line 94: | Line 112: | ||
|} | |} | ||
| − | + | == Datapoints == | |
{| class="wikitable" | {| class="wikitable" | ||
| Line 281: | Line 299: | ||
|R | |R | ||
|alarm is not partially armed | |alarm is not partially armed | ||
| + | |- | ||
| + | |||
| + | |rowspan="1"|a<n>.name<sup>[[#note|[Note]]]</sup> | ||
| + | |<text> | ||
| + | |R | ||
| + | |area name | ||
|- | |- | ||
| Line 310: | Line 334: | ||
|output label in ascii format | |output label in ascii format | ||
|- | |- | ||
| + | |||
| + | |rowspan="1"|o<n>.name<sup>[[#note|[Note]]]</sup> | ||
| + | |<text> | ||
| + | |R | ||
| + | |output name | ||
| + | |- | ||
| + | |||
|rowspan="4"|i<n>.state | |rowspan="4"|i<n>.state | ||
| Line 375: | Line 406: | ||
|- | |- | ||
| + | |rowspan="1"|i<n>.name<sup>[[#note|[Note]]]</sup> | ||
| + | |<text> | ||
| + | |R | ||
| + | |input name | ||
| + | |- | ||
| + | |||
| + | |rowspan="4"|ti<n>.state | ||
| + | |closed | ||
| + | |R | ||
| + | |trouble input is closed | ||
| + | |- | ||
| + | |open | ||
| + | |R | ||
| + | |trouble input in open | ||
| + | |- | ||
| + | |short | ||
| + | |R | ||
| + | |trouble input is in shortcut state | ||
| + | |- | ||
| + | |tamper | ||
| + | |R | ||
| + | |trouble input is in tamper state | ||
| + | |- | ||
| + | |||
| + | |rowspan="2"|ti<n>.closed | ||
| + | |1 | ||
| + | |R | ||
| + | |trouble input is closed | ||
| + | |- | ||
| + | |0 | ||
| + | |R | ||
| + | |trouble input is open | ||
| + | |- | ||
| + | |||
| + | |rowspan="1"|ti<n>.ascii | ||
| + | |<text> | ||
| + | |R | ||
| + | |trouble input label in ascii format | ||
| + | |- | ||
| + | |||
| + | |rowspan="2"|ti<n>.bypass.state.bypassed | ||
| + | |1 | ||
| + | |R | ||
| + | |trouble input is bypassed | ||
| + | |- | ||
| + | |0 | ||
| + | |R | ||
| + | |trouble input is not bypassed | ||
| + | |- | ||
| + | |||
| + | |rowspan="2"|ti<n>.bypass.state.bypasslatched | ||
| + | |1 | ||
| + | |R | ||
| + | |trouble input is bypass latched | ||
| + | |- | ||
| + | |0 | ||
| + | |R | ||
| + | |trouble input is not bypass latched | ||
| + | |- | ||
| + | |||
| + | |rowspan="2"|ti<n>.bypass.state.sirenlockout | ||
| + | |1 | ||
| + | |R | ||
| + | |trouble input is siren lockout state | ||
| + | |- | ||
| + | |0 | ||
| + | |R | ||
| + | |trouble input is not in siren lockout state | ||
| + | |- | ||
| + | |||
| + | |rowspan="1"|ti<n>.name<sup>[[#note|[Note]]]</sup> | ||
| + | |<text> | ||
| + | |R | ||
| + | |trouble input name | ||
| + | |- | ||
| + | |||
| + | |rowspan="10"|d<n>.lock.state | ||
| + | |locked | ||
| + | |R | ||
| + | |door is locked | ||
| + | |- | ||
| + | |unlockedbyuseraccess | ||
| + | |R | ||
| + | |door is unlocked by user access | ||
| + | |- | ||
| + | |unlockedbyschedule | ||
| + | |R | ||
| + | |door is unlocked by schedule | ||
| + | |- | ||
| + | |unlockedbyusertimed | ||
| + | |R | ||
| + | |door is unlocked by user timed | ||
| + | |- | ||
| + | |unlockedbyandlatched | ||
| + | |R | ||
| + | |door is unlocked by and latched | ||
| + | |- | ||
| + | |unlockedbyrex | ||
| + | |R | ||
| + | |door is unlocked by rex | ||
| + | |- | ||
| + | |unlockedbyren | ||
| + | |R | ||
| + | |door is unlocked by ren | ||
| + | |- | ||
| + | |unlockedbykeypadmenu | ||
| + | |R | ||
| + | |door is unlocked by keypad menu | ||
| + | |- | ||
| + | |unlockedbyarea | ||
| + | |R | ||
| + | |door is unlocked by area | ||
| + | |- | ||
| + | |unlockedbyfirealarm | ||
| + | |R | ||
| + | |door is unlocked by fire alarm | ||
| + | |- | ||
| + | |||
| + | |rowspan="2"|d<n>.locked | ||
| + | |1 | ||
| + | |R | ||
| + | |door is locked | ||
| + | |- | ||
| + | |0 | ||
| + | |R | ||
| + | | door is unlocked | ||
| + | |- | ||
| + | |||
| + | |rowspan="5"|d<n>.state | ||
| + | |closed | ||
| + | |R | ||
| + | |door is closed | ||
| + | |- | ||
| + | |open | ||
| + | |R | ||
| + | |door is open | ||
| + | |- | ||
| + | |openalert | ||
| + | |R | ||
| + | |door is open alert state | ||
| + | |- | ||
| + | |leftopen | ||
| + | |R | ||
| + | |door is left open state | ||
| + | |- | ||
| + | |forcedopen | ||
| + | |R | ||
| + | |door is forced open state | ||
| + | |- | ||
| + | |||
| + | |rowspan="1"|d<n>.name<sup>[[#note|[Note]]]</sup> | ||
| + | |<text> | ||
| + | |R | ||
| + | |door name | ||
| + | |- | ||
| + | |||
| + | |rowspan="7"|a<n> | ||
| + | |arm | ||
| + | |W | ||
| + | |arm area | ||
| + | |- | ||
| + | |armforce | ||
| + | |W | ||
| + | |arm area in force mode | ||
| + | |- | ||
| + | |armstay | ||
| + | |W | ||
| + | |arm area in stay mode | ||
| + | |- | ||
| + | |arminstant | ||
| + | |W | ||
| + | |arm area in instant mode | ||
| + | |- | ||
| + | |disarm | ||
| + | |W | ||
| + | |disarm area | ||
| + | |- | ||
| + | |disarm24h | ||
| + | |W | ||
| + | |disarm area | ||
| + | |- | ||
| + | |disarmall | ||
| + | |W | ||
| + | |disarm all area | ||
| + | |- | ||
| + | |||
| + | |rowspan="3"|o<n> | ||
| + | |on | ||
| + | |W | ||
| + | |output on | ||
| + | |- | ||
| + | |off | ||
| + | |W | ||
| + | |output off | ||
| + | |- | ||
| + | |ontimed-<seconds> | ||
| + | |W | ||
| + | |output on for a number of seconds equals to <seconds> E.G. ''o.ontimed-7'', means on for 7 seconds. | ||
| + | |- | ||
| + | |||
| + | |rowspan="3"|i<n> | ||
| + | |removebypass | ||
| + | |W | ||
| + | |remove bypass input | ||
| + | |- | ||
| + | |tempbypass | ||
| + | |W | ||
| + | |temporary bypass input | ||
| + | |- | ||
| + | |bypass | ||
| + | |W | ||
| + | |bypass for input | ||
| + | |- | ||
| + | |||
| + | |rowspan="3"|ti<n> | ||
| + | |removebypass | ||
| + | |W | ||
| + | |remove bypass trouble input | ||
| + | |- | ||
| + | |tempbypass | ||
| + | |W | ||
| + | |temporary bypass trouble input | ||
| + | |- | ||
| + | |bypass | ||
| + | |W | ||
| + | |bypass for trouble input | ||
| + | |- | ||
| + | |||
| + | |rowspan="3"|d<n> | ||
| + | |lock | ||
| + | |W | ||
| + | |lock door | ||
| + | |- | ||
| + | |unlock | ||
| + | |W | ||
| + | |unlock door | ||
| + | |- | ||
| + | |unlocklatched | ||
| + | |W | ||
| + | |unlock latched door | ||
| + | |- | ||
| + | |||
| + | |rowspan="1"|v<n> | ||
| + | |get | ||
| + | |W | ||
| + | |get the the value of the variable with index <n>. The value of variabile will be written in a datapoint v<n> = <value> | ||
| + | |- | ||
| + | |||
| + | |rowspan="1"|v<n> | ||
| + | |value-<value> | ||
| + | |W | ||
| + | |set the the value of the variable with index <n>. | ||
| + | |- | ||
| + | |||
| + | |} | ||
| + | <span id="note"> | ||
| + | ;Note: Names of areas, inputs, trouble inputs, outputs, doors are imported from a configuration file as described later in this application note. | ||
| + | </span> | ||
| + | |||
| + | == CSV configuration files import == | ||
| + | HSYCO can import the names of areas, inputs, trouble inputs, outputs, doors from a CSV file(s). The CSV file(s) could be easily download from the ICT Protege software. | ||
| + | This file(s) they are not mandatory. | ||
| + | |||
| + | The csv file(s) must have the same name of the id of the Protege I/O server plus the extension .csv | ||
| + | E.G. The I/O server id is pro1, the csv file name must be: pro1.csv | ||
| + | |||
| + | The csv file(s) must be copied in the folder protege/csv | ||
| + | E.G. Let's suppose to have to 2 Protege I/O servers called "pro1" and "pro2". Using the File Manager we have to create the folder "protege" in Hsyco's main folder, then the folder "csv" inside the "protege" folder, then 2 files called "pro1.csv" a "pro2.csv" should be copied inside this folder. | ||
| + | |||
| + | The csv file must have this format: | ||
| + | |||
| + | <pre> | ||
| + | # Item Types | ||
| + | # 0 = Controllers | ||
| + | # 1 = Doors | ||
| + | # 2 = Areas | ||
| + | # 3 = Outputs (PGM) | ||
| + | # 4 = Zones (Inputs | ||
| + | # 5 = Variables | ||
| + | # 6 = Trouble Inputs | ||
| + | # Item Type,Item ID,Controller ID,Name 2,Opt1 | ||
| + | 1,0,0,Door 1, | ||
| + | 1,1,0,Door 2, | ||
| + | 2,0,0,CP1: Area1, | ||
| + | 2,1,0,Area2, | ||
| + | 3,0,0, CP1 Bell 1, | ||
| + | 3,1,0, CP1 Relay 1, | ||
| + | 3,2,0, CP1 Relay 2, | ||
| + | 4,209,0,GX IX1 VirtInput 2, | ||
| + | 4,210,0,GX IX1 VirtInput 3, | ||
| + | 4,211,0,GX IX1 VirtInput 4, | ||
| + | 4,212,0,GX IX1 VirtInput 5, | ||
| + | 6,0,0, CP1 12V Supply Failure, | ||
| + | 6,1,0, CP1 Real Time Clock Not Set, | ||
| + | 6,2,0, CP1 Service Report Test | ||
| + | </pre> | ||
| + | |||
| + | == UISET Actions == | ||
| + | |||
| + | {| class="wikitable" | ||
| + | !ID | ||
| + | !Attribute | ||
| + | !colspan="2"|Set to | ||
| + | |- | ||
| + | |log | ||
| + | |value | ||
| + | |colspan="2"|latest security log lines (as many as specified by the 'logsize' option) | ||
| + | |- | ||
| + | |log0 | ||
| + | |value | ||
| + | |colspan="2"|latest line of the security log when a new entry is added, set back to blank after a short period | ||
| + | |- | ||
| + | |a<n>.name | ||
| + | |value | ||
| + | |colspan="2"|name assigned to area <n> | ||
| + | |- | ||
| + | |a<n>.state | ||
| + | |value | ||
| + | |colspan="2"|area state value<n> | ||
| + | |- | ||
| + | |a<n>.tamper.state | ||
| + | |value | ||
| + | |colspan="2"|area tamper state value<n> | ||
| + | |- | ||
| + | |o<n>.name | ||
| + | |value | ||
| + | |colspan="2"|name assigned to output <n> | ||
| + | |- | ||
| + | |o<n>.state | ||
| + | |value | ||
| + | |colspan="2"|output state value<n> | ||
| + | |- | ||
| + | |i<n>.name | ||
| + | |value | ||
| + | |colspan="2"|name assigned to input <n> | ||
| + | |- | ||
| + | |i<n>.state | ||
| + | |value | ||
| + | |colspan="2"|input state value<n> | ||
| + | |- | ||
| + | |ti<n>.name | ||
| + | |value | ||
| + | |colspan="2"|name assigned to trouble input <n> | ||
| + | |- | ||
| + | |ti<n>.state | ||
| + | |value | ||
| + | |colspan="2"|trouble input state value<n> | ||
| + | |- | ||
| + | |d<n>.name | ||
| + | |value | ||
| + | |colspan="2"|name assigned to door <n> | ||
| + | |- | ||
| + | |d<n>.state | ||
| + | |value | ||
| + | |colspan="2"|door state value <n> | ||
| + | |- | ||
| + | |d<n>.lock.state | ||
| + | |value | ||
| + | |colspan="2"|door lock state value <n> | ||
| + | |- | ||
| + | |rowspan="2"|connection.offline | ||
| + | |rowspan="2"|visible | ||
| + | |true | ||
| + | |when datapoint connection = offline | ||
| + | |- | ||
| + | |false | ||
| + | |when datapoint connection = online | ||
| + | |- | ||
| + | |rowspan="2"|connection.online | ||
| + | |rowspan="2"|visible | ||
| + | |true | ||
| + | |when datapoint connection = online | ||
| + | |- | ||
| + | |false | ||
| + | |when datapoint connection = offline | ||
| + | |- | ||
| + | |rowspan="2"|<datapoint_id>.1 | ||
| + | |rowspan="2"|visible | ||
| + | |true | ||
| + | |when datapoint with ID <datapoint_id> has value '1' | ||
| + | |- | ||
| + | |false | ||
| + | |when datapoint with ID <datapoint_id> has value '0' | ||
| + | |- | ||
| + | |rowspan="2"|<datapoint_id>.0 | ||
| + | |rowspan="2"|visible | ||
| + | |true | ||
| + | |when datapoint with ID <datapoint_id> has value '0' | ||
| + | |- | ||
| + | |false | ||
| + | |when datapoint with ID <datapoint_id> has value '1' | ||
|} | |} | ||
| + | |||
| + | == Log Files == | ||
| + | If a Protege anti-intrusion unit is connected to HSYCO, the security.log file will be written in the same directories as the daily log files and will include the log entries received by the panel. | ||
| + | |||
| + | This file is never overwritten or deleted from HSYCO SERVER. | ||
| + | |||
| + | == Release Notes == | ||
| + | === 3.7.0 === | ||
| + | *initial version release | ||
| + | |||
| + | ---- | ||
| + | |||
| + | |||
| + | ''Protege is a registered trademark of Integrated Control Technology Limited'' | ||
Latest revision as of 08:09, 29 August 2019
Protege is a server based architecture enabling you to securely manage, control and monitor a number of users, doors, areas, and other devices. The integration with HSYCO can be accomplished with a TCP/IP network connection.
Contents
Protege Configuration
ProtegeGXServer needs to be configured to accept a connection on a defined TCP/IP port with the ICT Automation and Control Service protocol.
- A PIN must be set (4 to 6 digits)
Open Programming > Services Select the controller associated to the Protege I/O Server Click "Add" to activate the "Automation and Control" service
- Under "Service Type /General" specify a name (freely choose), for the main and the second language.
- Under "Service Type /Type" select "Automation and Control" then set "Service Mode" to "1 - Start with Controller OS"
- Under "General / Configuration" select "TCP/I" then specify a "Port Number". Set "Encryption Level" and "Checksum Type" to "None"
- Under "General / Options" enable "Allow Status Requests when not Logged In", "Use Logon Lock Out Timer if Incorrect PIN is Supplied", "Ack Command"
This driver works with Little Endian format
Click "Save" to confirm. Right click on the service and select "Start Service"
HSYCO Configuration
Add a PROTEGE I/O Server in the I/O Servers section of the Settings and set its parameters:
Communication
- IP Address: the ICT Protege Server panel address
- IP Port: TCP/IP port enabled on the ICT Protege Server
High Availability
- Shutdown when inactive: defaults to true.
Options
| ID | Default | Values | Description |
|---|---|---|---|
| pin | pin | the user PIN that the driver uses when sending commands to the Protege system. It must be a valid user code, able to engage and disengage the panel. | |
| startupevents | false | true | generate IO events also during the driver’s start-up phase |
| false | start generating events only after HSYCO is aligned with the current status of the system | ||
| gui | true | true | enable support of the tecnoalarm Web interface object |
| false | disable support of the tecnoalarm Web interface object | ||
| debug | false | true | generates additional logs that can be viewed in verbose mode |
| false | debug logging disabled | ||
| areaslist | string | list of all the areas that are declared on the panel. Areas could not be consecutive and special characters "-" and ";" are used for intervals definition. E.G. 0-3;5-9 means areas from 0 to 3, from 5 to 9. E.G. 4;15 means area number 4 and number 15 | |
| inputslist | string | list of all the inputs that are declared on the panel. Inputs could not be consecutive and special characters "-" and ";" are used for intervals definition. E.G. 0-3;5-9 means inputs from 0 to 3, from 5 to 9. E.G. 4;15 means input number 4 and input 15 | |
| outputslist | string | list of all the outputs that are declared on the panel. Outputs could not be consecutive and special characters "-" and ";" are used for intervals definition. E.G. 0-3;5-9 means outputs from 0 to 3, from 5 to 9. E.G. 4;15 means output number 4 and output 15 | |
| doorslist | string | list of all the doors that are declared on the panel. Doors could not be consecutive and special characters "-" and ";" are used for intervals definition. E.G. 0-3;5-9 means doors from 0 to 3, from 5 to 9. E.G. 4;15 means door number 4 and door 15 | |
| troubleinputslist | string | list of all the trouble inputs that are declared on the panel. Trouble inputs could not be consecutive and special characters "-" and ";" are used for intervals definition. E.G. 0-3;5-9 means trouble inputs from 0 to 3, from 5 to 9. E.G. 4;15 means trouble input number 4 and trouble input 15 |
Datapoints
| ID | Value | R/W | Description |
|---|---|---|---|
| connection | online | R | connection established |
| offline | R | connection failed | |
| panel.firmware.build | <text> | R | firmware build of the panel |
| panel.firmware.type | <text> | R | firmware type of the panel |
| panel.firmware.version | <text> | R | firmware version of the panel |
| panel.hardware.version | <text> | R | hardware version of the panel |
| panel.serial.number | <text> | R | serial number of the panel |
| a<n>.armed | 1 | R | area is armed |
| 0 | R | area is disarmed | |
| a<n>.state | armed | R | area is armed |
| disarmed | R | area is disarmed | |
| inputsopen | R | area is in inputs open state | |
| trouble | R | area is in trouble state | |
| bypasserror | R | area is in bypass error state | |
| bypasswarning | R | area is in bypass warning state | |
| usercountnotzero | R | area is in user count not zero state | |
| exitdelay | R | area is in exit delay state | |
| entrydelay | R | area is in entry delay state | |
| disarmdelay | R | area is in disarm delay state | |
| codedelay | R | area is in code delay state | |
| a<n>.tamper.state | armed | R | area tamper is armed |
| disarmed | R | area tamper is disarmed | |
| busy | R | area tamper is busy | |
| a<n>.state.flags.alarm.activated | 1 | R | area alarm activated |
| 0 | R | area alarm is not active | |
| a<n>.state.flags.siren.activated | 1 | R | area siren activated |
| 0 | R | area siren is not active | |
| a<n>.state.flags.alarms.in.memory | 1 | R | at least one area alarm in memory |
| 0 | R | no area alarms in memory | |
| a<n>.state.flags.remote.armed | 1 | R | area remotely armed |
| 0 | R | alarm is not remotely armed | |
| a<n>.state.flags.force.armed | 1 | R | area forced armed |
| 0 | R | alarm is not forced armed | |
| a<n>.state.flags.instant.armed | 1 | R | area instant armed |
| 0 | R | alarm is not instant armed | |
| a<n>.state.flags.partial.armed | 1 | R | area partially armed |
| 0 | R | alarm is not partially armed | |
| a<n>.name[Note] | <text> | R | area name |
| o<n>.state | off | R | output is off |
| on | R | output is on | |
| onpulsed | R | output is in on pulsed state | |
| ontimed | R | output is in on timed state | |
| onpulsedtimed | R | output is in on pulsed timed state | |
| o<n>.ascii | <text> | R | output label in ascii format |
| o<n>.name[Note] | <text> | R | output name |
| i<n>.state | closed | R | input is closed |
| open | R | input in open | |
| short | R | input is in shortcut state | |
| tamper | R | input is in tamper state | |
| i<n>.closed | 1 | R | input is closed |
| 0 | R | input is open | |
| i<n>.ascii | <text> | R | input label in ascii format |
| i<n>.bypass.state.bypassed | 1 | R | input is bypassed |
| 0 | R | input is not bypassed | |
| i<n>.bypass.state.bypasslatched | 1 | R | input is bypass latched |
| 0 | R | input is not bypass latched | |
| i<n>.bypass.state.sirenlockout | 1 | R | input is siren lockout state |
| 0 | R | input is not in siren lockout state | |
| i<n>.name[Note] | <text> | R | input name |
| ti<n>.state | closed | R | trouble input is closed |
| open | R | trouble input in open | |
| short | R | trouble input is in shortcut state | |
| tamper | R | trouble input is in tamper state | |
| ti<n>.closed | 1 | R | trouble input is closed |
| 0 | R | trouble input is open | |
| ti<n>.ascii | <text> | R | trouble input label in ascii format |
| ti<n>.bypass.state.bypassed | 1 | R | trouble input is bypassed |
| 0 | R | trouble input is not bypassed | |
| ti<n>.bypass.state.bypasslatched | 1 | R | trouble input is bypass latched |
| 0 | R | trouble input is not bypass latched | |
| ti<n>.bypass.state.sirenlockout | 1 | R | trouble input is siren lockout state |
| 0 | R | trouble input is not in siren lockout state | |
| ti<n>.name[Note] | <text> | R | trouble input name |
| d<n>.lock.state | locked | R | door is locked |
| unlockedbyuseraccess | R | door is unlocked by user access | |
| unlockedbyschedule | R | door is unlocked by schedule | |
| unlockedbyusertimed | R | door is unlocked by user timed | |
| unlockedbyandlatched | R | door is unlocked by and latched | |
| unlockedbyrex | R | door is unlocked by rex | |
| unlockedbyren | R | door is unlocked by ren | |
| unlockedbykeypadmenu | R | door is unlocked by keypad menu | |
| unlockedbyarea | R | door is unlocked by area | |
| unlockedbyfirealarm | R | door is unlocked by fire alarm | |
| d<n>.locked | 1 | R | door is locked |
| 0 | R | door is unlocked | |
| d<n>.state | closed | R | door is closed |
| open | R | door is open | |
| openalert | R | door is open alert state | |
| leftopen | R | door is left open state | |
| forcedopen | R | door is forced open state | |
| d<n>.name[Note] | <text> | R | door name |
| a<n> | arm | W | arm area |
| armforce | W | arm area in force mode | |
| armstay | W | arm area in stay mode | |
| arminstant | W | arm area in instant mode | |
| disarm | W | disarm area | |
| disarm24h | W | disarm area | |
| disarmall | W | disarm all area | |
| o<n> | on | W | output on |
| off | W | output off | |
| ontimed-<seconds> | W | output on for a number of seconds equals to <seconds> E.G. o.ontimed-7, means on for 7 seconds. | |
| i<n> | removebypass | W | remove bypass input |
| tempbypass | W | temporary bypass input | |
| bypass | W | bypass for input | |
| ti<n> | removebypass | W | remove bypass trouble input |
| tempbypass | W | temporary bypass trouble input | |
| bypass | W | bypass for trouble input | |
| d<n> | lock | W | lock door |
| unlock | W | unlock door | |
| unlocklatched | W | unlock latched door | |
| v<n> | get | W | get the the value of the variable with index <n>. The value of variabile will be written in a datapoint v<n> = <value> |
| v<n> | value-<value> | W | set the the value of the variable with index <n>. |
- Note
- Names of areas, inputs, trouble inputs, outputs, doors are imported from a configuration file as described later in this application note.
CSV configuration files import
HSYCO can import the names of areas, inputs, trouble inputs, outputs, doors from a CSV file(s). The CSV file(s) could be easily download from the ICT Protege software. This file(s) they are not mandatory.
The csv file(s) must have the same name of the id of the Protege I/O server plus the extension .csv E.G. The I/O server id is pro1, the csv file name must be: pro1.csv
The csv file(s) must be copied in the folder protege/csv E.G. Let's suppose to have to 2 Protege I/O servers called "pro1" and "pro2". Using the File Manager we have to create the folder "protege" in Hsyco's main folder, then the folder "csv" inside the "protege" folder, then 2 files called "pro1.csv" a "pro2.csv" should be copied inside this folder.
The csv file must have this format:
# Item Types # 0 = Controllers # 1 = Doors # 2 = Areas # 3 = Outputs (PGM) # 4 = Zones (Inputs # 5 = Variables # 6 = Trouble Inputs # Item Type,Item ID,Controller ID,Name 2,Opt1 1,0,0,Door 1, 1,1,0,Door 2, 2,0,0,CP1: Area1, 2,1,0,Area2, 3,0,0, CP1 Bell 1, 3,1,0, CP1 Relay 1, 3,2,0, CP1 Relay 2, 4,209,0,GX IX1 VirtInput 2, 4,210,0,GX IX1 VirtInput 3, 4,211,0,GX IX1 VirtInput 4, 4,212,0,GX IX1 VirtInput 5, 6,0,0, CP1 12V Supply Failure, 6,1,0, CP1 Real Time Clock Not Set, 6,2,0, CP1 Service Report Test
UISET Actions
| ID | Attribute | Set to | |
|---|---|---|---|
| log | value | latest security log lines (as many as specified by the 'logsize' option) | |
| log0 | value | latest line of the security log when a new entry is added, set back to blank after a short period | |
| a<n>.name | value | name assigned to area <n> | |
| a<n>.state | value | area state value<n> | |
| a<n>.tamper.state | value | area tamper state value<n> | |
| o<n>.name | value | name assigned to output <n> | |
| o<n>.state | value | output state value<n> | |
| i<n>.name | value | name assigned to input <n> | |
| i<n>.state | value | input state value<n> | |
| ti<n>.name | value | name assigned to trouble input <n> | |
| ti<n>.state | value | trouble input state value<n> | |
| d<n>.name | value | name assigned to door <n> | |
| d<n>.state | value | door state value <n> | |
| d<n>.lock.state | value | door lock state value <n> | |
| connection.offline | visible | true | when datapoint connection = offline |
| false | when datapoint connection = online | ||
| connection.online | visible | true | when datapoint connection = online |
| false | when datapoint connection = offline | ||
| <datapoint_id>.1 | visible | true | when datapoint with ID <datapoint_id> has value '1' |
| false | when datapoint with ID <datapoint_id> has value '0' | ||
| <datapoint_id>.0 | visible | true | when datapoint with ID <datapoint_id> has value '0' |
| false | when datapoint with ID <datapoint_id> has value '1' | ||
Log Files
If a Protege anti-intrusion unit is connected to HSYCO, the security.log file will be written in the same directories as the daily log files and will include the log entries received by the panel.
This file is never overwritten or deleted from HSYCO SERVER.
Release Notes
3.7.0
- initial version release
Protege is a registered trademark of Integrated Control Technology Limited