Difference between revisions of "SSH"
(Created page with "[http://www.arteco-global.com Arteco Everywhere] is a general purpose digital input-output Ethernet controller. It is available in two versions, a 4 inputs, 4 outputs module,...") |
|||
| (44 intermediate revisions by 5 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | Secure Shell (SSH) is a cryptographic network protocol for secure data communication, remote command-line login, remote command execution, and other secure network services between two networked computers that connects, via a secure channel over an insecure network, a server and a client (running SSH server and SSH client programs, respectively). | |
| − | + | The best-known application of the protocol is for access to shell accounts on Unix-like operating systems, but it can also be used in a similar fashion for accounts on Windows. | |
| − | + | It was designed as a replacement for Telnet and other insecure remote shell protocols, which send information, notably passwords, in plaintext, rendering them susceptible to interception and disclosure using packet analysis. | |
| + | |||
| + | The encryption used by SSH is intended to provide confidentiality and integrity of data over an unsecured network, such as the Internet. | ||
| + | |||
| + | The SSH I/O Server implements the SSH-2 version of the protocol, and supports remote command execution and the SCP protocol for bidirectional file transfer. It uses HSYCO data points to execute commands and return command status, making it easy to use the SSH protocol in EVENTS, as well as JavaScript and Java. | ||
| + | |||
| + | The SSH I/O Server establishes a single SSH connection to the server, using keyboard-interactive or password-based authentication, and creates individual sessions to execute single commands. | ||
| + | |||
| + | {{tip|Commands are executed sequentially, not in parallel.}} | ||
| − | |||
[[Category:I/O Server]] | [[Category:I/O Server]] | ||
| − | == | + | == SSH Remote Server Configuration == |
| − | |||
| − | The user and password | + | The remote system should be configured to accept the SSH connection from the HSYCO server using the username and password defined in the I/O Server’s options. |
| + | |||
| + | If you need to execute operating system’s commands with superuser privileges (with the sudo program), the remote user name defined with the user option in the SSH I/O Server configuration must be allowed to execute “sudo” commands without asking for a password. | ||
| + | |||
| + | For example, if the user is hsyco, you could add the line: | ||
| + | hsyco ALL=(ALL:ALL) NOPASSWD: ALL | ||
| + | |||
| + | at the end of the /etc/sudoers file (use the visudo command to edit the /etc/sudoers file). | ||
| + | |||
| + | {{tip|If the username and password are correct, but the remote server refuses the authentication (you will see a "Password authentication failed." message in the logs and the I/O Server will keep restarting), the most probable cause is that the remote SSH server is configured to refuse the "keyboard-interactive" or "password" authentication type. To make it work, you should change the remote server's configuration to enable either keyboard-interactive or password authentication.}} | ||
== HSYCO Configuration == | == HSYCO Configuration == | ||
| + | Add an SSH I/O Server in the [[Settings#I/O Servers|I/O Servers section of the Settings]] and set its parameters: | ||
| + | |||
| + | {{note|Note that the SSH I/O Server doesn't count in the I/O servers license total, so you don't need an extra I/O Server license to use SSH with HSYCO.}} | ||
| + | |||
| + | === Communication === | ||
| + | *'''IP Address''': IP address of the remote device | ||
| + | *'''IP Port''': IP port enabled for the SSH service on the remote device, leave blank for default port 22. | ||
| + | |||
| + | === Authentication === | ||
| + | *'''User''': username for authentication on the remote device | ||
| + | *'''Password''': password. A PEM file name (containing a private key) can be used instead of password for public-key authentication | ||
| + | |||
| + | === High Availability === | ||
| + | *'''Shutdown when inactive''': defaults to false. | ||
=== Options === | === Options === | ||
| Line 23: | Line 52: | ||
!Values | !Values | ||
!Description | !Description | ||
| + | |||
|- | |- | ||
| − | + | |rowspan="3"|stdout | |
| − | |rowspan=" | + | |rowspan="3"|true |
| − | |rowspan=" | ||
|true | |true | ||
| − | |generate IO events | + | |when a remote command is executed, generate IO events containing the command's standard output and standard error streams |
|- | |- | ||
|false | |false | ||
| − | | | + | |do not generate IO events of the command's output and error streams |
|- | |- | ||
| + | |line | ||
| + | |IO events are generated for each line of the command's standard output and standard error streams | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
|- | |- | ||
| − | + | |rowspan="2"|persistentconnection | |
| − | |rowspan="2"| | + | |rowspan="2"|true |
| − | |rowspan="2"| | ||
|true | |true | ||
| − | | | + | |the I/O Server establishes the SSH connection at start-up and keeps it open across multiple commands. Commands execution is faster, but a small amount of network traffic is present, even when no commands are executed, to keep the connection open |
|- | |- | ||
|false | |false | ||
| − | | | + | |the I/O Server will not establish a connection to the remote server until a command is executed. The connection is closed 30 seconds after the execution of the last command |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
|} | |} | ||
== Datapoints == | == Datapoints == | ||
| − | |||
| − | |||
| − | |||
| − | |||
{| class="wikitable" | {| class="wikitable" | ||
| − | !ID | + | !width=160 |ID |
| − | !Value | + | !width=160 |Value |
!R/W | !R/W | ||
!Description | !Description | ||
| + | |||
|- | |- | ||
| − | + | |rowspan="3" |connection | |
| − | |rowspan=" | ||
|online | |online | ||
|R | |R | ||
| − | |connection established | + | |SSH connection established (with successful authentication) |
|- | |- | ||
|offline | |offline | ||
|R | |R | ||
| − | | | + | |SSH connection closed |
|- | |- | ||
| + | |close | ||
| + | |W | ||
| + | |closes the SSH connection | ||
| − | |rowspan="2" | | + | |- |
| − | | | + | |exec |
| + | |rowspan="2" |<command string> | ||
| + | |rowspan="2" |W | ||
| + | |rowspan="2" |executes the command passed as value. | ||
| + | An optional command execution timeout in seconds defines how long the command is allowed to wait reading from stdout and stderr. The default is 30 seconds | ||
| + | |- | ||
| + | |exec.<timeout> | ||
| + | |- | ||
| + | |exec | ||
| + | |<exit status> | ||
|R | |R | ||
| − | | | + | | |
| + | * the command's exit status number | ||
| + | * "error" if the command could not be sent to the remote server | ||
| + | * "null" if the remote server failed to return an exit status code (some SSH servers do not return the exit status) | ||
| + | |||
|- | |- | ||
| − | | | + | |err |
| + | |<error stream> | ||
|R | |R | ||
| − | | | + | |the executed command standard error stream, with lines separated by <nowiki>"<br>"</nowiki>, or an empty string if the command's error stream is empty |
| + | |||
|- | |- | ||
| + | |out | ||
| + | |<error stream> | ||
| + | |R | ||
| + | |the executed command standard output stream, with lines separated by <nowiki>"<br>"</nowiki>, or an empty string if the command's output stream is empty | ||
| − | |||
| − | |||
| − | |||
| − | |||
|- | |- | ||
| + | |rowspan="2" |get | ||
| + | |<source> <destination> | ||
|W | |W | ||
| − | | | + | |retrieves the remote source file and writes it locally to the destination path name.<br>The source and destination string in value should be separated by one or more spaces.<br>Always use the "/" character as path separator.<br>Use "\" as the escape character if the file names have spaces.<br>The destination directory must exist and cannot be outside of the HSYCO's base directory, or the command will fail. If the destination name doesn't have a path, the file will be written to the HSYCO's base directory |
|- | |- | ||
| + | |<exit status> | ||
| + | |R | ||
| + | | | ||
| + | * the total number of transferred bytes (should be equal to the actual file size) | ||
| + | * "error" if the file transfer failed | ||
| − | |||
| − | |||
| − | |||
|- | |- | ||
| + | |rowspan="2" |put | ||
| + | |<source> <destination> | ||
|W | |W | ||
| − | | | + | |copy the local source file to the remote server's destination path name.<br>The source and destination string in value should be separated by one or more spaces.<br>Always use the "/" character as path separator.<br>Use "\" as the escape character if the file names have spaces.<br>The source file cannot be outside of the HSYCO's base directory, or the command will fail. If the source name doesn't have a path, the file will be read from the HSYCO's base directory.<br>The file will be saved to the remote server with 600 (owner's only read and write) permission |
|- | |- | ||
| + | |<exit status> | ||
| + | |R | ||
| + | | | ||
| + | * the total number of transferred bytes (should be equal to the actual file size) | ||
| + | * "error" if the file transfer failed | ||
| − | | | + | |- |
| + | |user | ||
| + | |<user name> | ||
|W | |W | ||
| − | | | + | |overrides the "user" configuration parameter. This command can only be used when persistentconnection=false, and becomes effective after the current connection is closed. Set <user name> to an empty string to restore the original settings |
| + | |||
|- | |- | ||
| + | |password | ||
| + | |<user password> | ||
| + | |W | ||
| + | |overrides the "password" configuration parameter. This command can only be used when persistentconnection=false, and becomes effective after the current connection is closed. Set <user password> to an empty string to restore the original settings. A PEM file name (containing a private key) can be used instead of password for public-key authentication | ||
| − | |||
| − | |||
| − | |||
|- | |- | ||
| + | |} | ||
| + | |||
| + | |||
| + | {{tip|The exec, err, out, get and put data points will trigger the IO events at the end of the command's execution even if the value is not changed. This allows you to easily intercept the exit status and other return information.}} | ||
| + | |||
| + | == Examples == | ||
| + | |||
| + | {{tip|In the following examples, we assume that the id of the SSH I/O Server is "ssh".}} | ||
| + | |||
| + | === Remote Command Execution === | ||
| + | |||
| + | Reboot a remote system at midnight. | ||
| + | |||
| + | <syntaxhighlight lang="javascript"> | ||
| + | TIME 0000 : IO ssh.exec = "sudo reboot" | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | Turn off screen at midnight. | ||
| − | + | <syntaxhighlight lang="javascript"> | |
| − | + | TIME 0000 : IO ssh.exec = "sudo vbetool dpms off" | |
| − | + | </syntaxhighlight> | |
| − | | | + | |
| + | Turn on screen at 7 o' clock. | ||
| + | |||
| + | <syntaxhighlight lang="javascript"> | ||
| + | TIME 0700 : IO ssh.exec = "sudo vbetool dpms on" | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | === File Transfer === | ||
| + | |||
| + | At midnight, copy HSYCO's internal database backup to a remote server. | ||
| + | |||
| + | <syntaxhighlight lang="javascript"> | ||
| + | TIME 0000 : IO ssh.put = "data_backup/hsyco.data /tmp/data_backup/hsyco.data", | ||
| + | IO ssh.put = "data_backup/hsyco.properties /tmp/data_backup/hsyco.properties", | ||
| + | IO ssh.put = "data_backup/hsyco.script /tmp/data_backup/hsyco.script" | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | === Interactive Remote Command Project === | ||
| + | |||
| + | Create a simple interactive command console in HSYCO. | ||
| + | |||
| + | |||
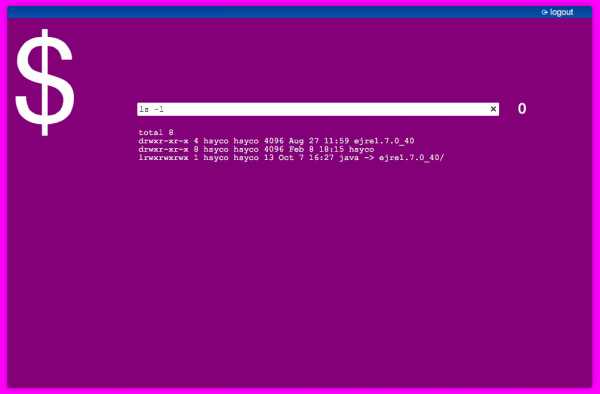
| + | [[File:SSH_example_inteactive_command_interface.png|border|600px|center]] | ||
| + | |||
| + | '''The project's file''' | ||
| − | + | <syntaxhighlight lang="text"> | |
| + | (#skin blue) | ||
| + | (#language it) | ||
| + | (#size 980x640) | ||
| + | (#style body-background-color=#FF00FF; pages-background-color=#770077) | ||
| + | (#uiset $exec.eraseicon=true) | ||
| − | + | (header SSH) | |
| − | + | (menu) | |
| + | (text!stderr r5c3;; (width:600px; text-align:left; height:400px; font-family:Courier New, Courier, monospace)) | ||
| + | (text!stdout r5c3;; (width:600px; text-align:left; height:400px; overflow:auto; font-family:Courier New, Courier, monospace)) | ||
| + | (input!$exec r4c3; (width:600px; font-family:Courier New, Courier, monospace); input) | ||
| + | (text r1c1; $; font-size:200px) | ||
| + | (text!exitcode r4c9;; font-size:24px) | ||
| + | (endofmenu) | ||
| + | </syntaxhighlight> | ||
| − | |||
| + | '''Events logic''' | ||
| − | + | <syntaxhighlight lang="javascript"> | |
| + | USER "$exec" : IO ssh.exec = $exec, UISET "$exec.focus" = true | ||
| + | IO ssh.out : UISET stdout.text = IO ssh.out | ||
| + | IO ssh.err : UISET stderr.text = IO ssh.err | ||
| + | IO ssh.exec : UISET exitcode.text = IO ssh.exec | ||
| + | </syntaxhighlight> | ||
== Release Notes == | == Release Notes == | ||
| − | === 3. | + | === 3.8.0 === |
| − | * | + | * a PEM file name (containing a private key) can be used instead of password for public-key authentication |
| − | + | === 3.7.0 === | |
| + | * the SSH I/O Server is now "free". Using it doesn't decrease the number of available I/O servers | ||
| + | * new exec.<timeout> data point. Sets the command execution timeout in seconds; defaults to 30 | ||
| + | * new connection = close command: closes the SSH connection | ||
| + | * new user = <user name> command; overrides the user configuration parameter | ||
| + | * new password = <user password> command; overrides the password configuration parameter | ||
| + | * new stdout=line option | ||
| − | + | === 3.4.0 === | |
| − | + | * added support for the "keyboard-interactive" authentication method | |
| + | === 3.3.0 === | ||
| + | * initial release | ||
Latest revision as of 16:51, 22 March 2023
Secure Shell (SSH) is a cryptographic network protocol for secure data communication, remote command-line login, remote command execution, and other secure network services between two networked computers that connects, via a secure channel over an insecure network, a server and a client (running SSH server and SSH client programs, respectively).
The best-known application of the protocol is for access to shell accounts on Unix-like operating systems, but it can also be used in a similar fashion for accounts on Windows.
It was designed as a replacement for Telnet and other insecure remote shell protocols, which send information, notably passwords, in plaintext, rendering them susceptible to interception and disclosure using packet analysis.
The encryption used by SSH is intended to provide confidentiality and integrity of data over an unsecured network, such as the Internet.
The SSH I/O Server implements the SSH-2 version of the protocol, and supports remote command execution and the SCP protocol for bidirectional file transfer. It uses HSYCO data points to execute commands and return command status, making it easy to use the SSH protocol in EVENTS, as well as JavaScript and Java.
The SSH I/O Server establishes a single SSH connection to the server, using keyboard-interactive or password-based authentication, and creates individual sessions to execute single commands.
![]() Commands are executed sequentially, not in parallel.
Commands are executed sequentially, not in parallel.
Contents
SSH Remote Server Configuration
The remote system should be configured to accept the SSH connection from the HSYCO server using the username and password defined in the I/O Server’s options.
If you need to execute operating system’s commands with superuser privileges (with the sudo program), the remote user name defined with the user option in the SSH I/O Server configuration must be allowed to execute “sudo” commands without asking for a password.
For example, if the user is hsyco, you could add the line:
hsyco ALL=(ALL:ALL) NOPASSWD: ALL
at the end of the /etc/sudoers file (use the visudo command to edit the /etc/sudoers file).
![]() If the username and password are correct, but the remote server refuses the authentication (you will see a "Password authentication failed." message in the logs and the I/O Server will keep restarting), the most probable cause is that the remote SSH server is configured to refuse the "keyboard-interactive" or "password" authentication type. To make it work, you should change the remote server's configuration to enable either keyboard-interactive or password authentication.
If the username and password are correct, but the remote server refuses the authentication (you will see a "Password authentication failed." message in the logs and the I/O Server will keep restarting), the most probable cause is that the remote SSH server is configured to refuse the "keyboard-interactive" or "password" authentication type. To make it work, you should change the remote server's configuration to enable either keyboard-interactive or password authentication.
HSYCO Configuration
Add an SSH I/O Server in the I/O Servers section of the Settings and set its parameters:
Communication
- IP Address: IP address of the remote device
- IP Port: IP port enabled for the SSH service on the remote device, leave blank for default port 22.
Authentication
- User: username for authentication on the remote device
- Password: password. A PEM file name (containing a private key) can be used instead of password for public-key authentication
High Availability
- Shutdown when inactive: defaults to false.
Options
| ID | Default | Values | Description |
|---|---|---|---|
| stdout | true | true | when a remote command is executed, generate IO events containing the command's standard output and standard error streams |
| false | do not generate IO events of the command's output and error streams | ||
| line | IO events are generated for each line of the command's standard output and standard error streams | ||
| persistentconnection | true | true | the I/O Server establishes the SSH connection at start-up and keeps it open across multiple commands. Commands execution is faster, but a small amount of network traffic is present, even when no commands are executed, to keep the connection open |
| false | the I/O Server will not establish a connection to the remote server until a command is executed. The connection is closed 30 seconds after the execution of the last command |
Datapoints
| ID | Value | R/W | Description |
|---|---|---|---|
| connection | online | R | SSH connection established (with successful authentication) |
| offline | R | SSH connection closed | |
| close | W | closes the SSH connection | |
| exec | <command string> | W | executes the command passed as value.
An optional command execution timeout in seconds defines how long the command is allowed to wait reading from stdout and stderr. The default is 30 seconds |
| exec.<timeout> | |||
| exec | <exit status> | R |
|
| err | <error stream> | R | the executed command standard error stream, with lines separated by "<br>", or an empty string if the command's error stream is empty |
| out | <error stream> | R | the executed command standard output stream, with lines separated by "<br>", or an empty string if the command's output stream is empty |
| get | <source> <destination> | W | retrieves the remote source file and writes it locally to the destination path name. The source and destination string in value should be separated by one or more spaces. Always use the "/" character as path separator. Use "\" as the escape character if the file names have spaces. The destination directory must exist and cannot be outside of the HSYCO's base directory, or the command will fail. If the destination name doesn't have a path, the file will be written to the HSYCO's base directory |
| <exit status> | R |
| |
| put | <source> <destination> | W | copy the local source file to the remote server's destination path name. The source and destination string in value should be separated by one or more spaces. Always use the "/" character as path separator. Use "\" as the escape character if the file names have spaces. The source file cannot be outside of the HSYCO's base directory, or the command will fail. If the source name doesn't have a path, the file will be read from the HSYCO's base directory. The file will be saved to the remote server with 600 (owner's only read and write) permission |
| <exit status> | R |
| |
| user | <user name> | W | overrides the "user" configuration parameter. This command can only be used when persistentconnection=false, and becomes effective after the current connection is closed. Set <user name> to an empty string to restore the original settings |
| password | <user password> | W | overrides the "password" configuration parameter. This command can only be used when persistentconnection=false, and becomes effective after the current connection is closed. Set <user password> to an empty string to restore the original settings. A PEM file name (containing a private key) can be used instead of password for public-key authentication |
![]() The exec, err, out, get and put data points will trigger the IO events at the end of the command's execution even if the value is not changed. This allows you to easily intercept the exit status and other return information.
The exec, err, out, get and put data points will trigger the IO events at the end of the command's execution even if the value is not changed. This allows you to easily intercept the exit status and other return information.
Examples
![]() In the following examples, we assume that the id of the SSH I/O Server is "ssh".
In the following examples, we assume that the id of the SSH I/O Server is "ssh".
Remote Command Execution
Reboot a remote system at midnight.
TIME 0000 : IO ssh.exec = "sudo reboot"Turn off screen at midnight.
TIME 0000 : IO ssh.exec = "sudo vbetool dpms off"Turn on screen at 7 o' clock.
TIME 0700 : IO ssh.exec = "sudo vbetool dpms on"File Transfer
At midnight, copy HSYCO's internal database backup to a remote server.
TIME 0000 : IO ssh.put = "data_backup/hsyco.data /tmp/data_backup/hsyco.data",
IO ssh.put = "data_backup/hsyco.properties /tmp/data_backup/hsyco.properties",
IO ssh.put = "data_backup/hsyco.script /tmp/data_backup/hsyco.script"Interactive Remote Command Project
Create a simple interactive command console in HSYCO.
The project's file
(#skin blue)
(#language it)
(#size 980x640)
(#style body-background-color=#FF00FF; pages-background-color=#770077)
(#uiset $exec.eraseicon=true)
(header SSH)
(menu)
(text!stderr r5c3;; (width:600px; text-align:left; height:400px; font-family:Courier New, Courier, monospace))
(text!stdout r5c3;; (width:600px; text-align:left; height:400px; overflow:auto; font-family:Courier New, Courier, monospace))
(input!$exec r4c3; (width:600px; font-family:Courier New, Courier, monospace); input)
(text r1c1; $; font-size:200px)
(text!exitcode r4c9;; font-size:24px)
(endofmenu)
Events logic
USER "$exec" : IO ssh.exec = $exec, UISET "$exec.focus" = true
IO ssh.out : UISET stdout.text = IO ssh.out
IO ssh.err : UISET stderr.text = IO ssh.err
IO ssh.exec : UISET exitcode.text = IO ssh.execRelease Notes
3.8.0
- a PEM file name (containing a private key) can be used instead of password for public-key authentication
3.7.0
- the SSH I/O Server is now "free". Using it doesn't decrease the number of available I/O servers
- new exec.<timeout> data point. Sets the command execution timeout in seconds; defaults to 30
- new connection = close command: closes the SSH connection
- new user = <user name> command; overrides the user configuration parameter
- new password = <user password> command; overrides the password configuration parameter
- new stdout=line option
3.4.0
- added support for the "keyboard-interactive" authentication method
3.3.0
- initial release