Difference between revisions of "Lares4"
| Line 3: | Line 3: | ||
== Configuration from Ksenia cloud == | == Configuration from Ksenia cloud == | ||
| − | You must firstly configure your panel in the web app at the following address https://<panel_ip_addrss> (the panel starts in DHCP mode so you | + | You must firstly configure your panel in the web app at the following address 'https://<panel_ip_addrss>' (the panel starts in DHCP mode so you have to find the relative IP address assigned). In the web app, select your panel and log into it with installer privileges, then go to settings. In settings, disable DHCP mode and set a static ip address, then disable HTTPS connection (you must select non-secure HTTP connection with port 80). When you have finished save your configuration. |
In alternative, you can configure your panel passing by Ksenia SecureWeb cloud. | In alternative, you can configure your panel passing by Ksenia SecureWeb cloud. | ||
Revision as of 13:03, 1 July 2021
The KSENIA lares 4.0 is a multi-area security system. The I/O Server has been tested on unit with firmware version 1.72.2 and web server version 1.32.7. Actually this driver runs only in HTTP mode (port 80 is set by default).
Contents
Configuration from Ksenia cloud
You must firstly configure your panel in the web app at the following address 'https://<panel_ip_addrss>' (the panel starts in DHCP mode so you have to find the relative IP address assigned). In the web app, select your panel and log into it with installer privileges, then go to settings. In settings, disable DHCP mode and set a static ip address, then disable HTTPS connection (you must select non-secure HTTP connection with port 80). When you have finished save your configuration. In alternative, you can configure your panel passing by Ksenia SecureWeb cloud.
HSYCO Configuration
Add a LARES4 I/O Server in the I/O Servers section of the Settings and set its parameters:
Communication
- IP Address: host name or IP address of the panel
- IP Port: leave it blank
Authentication
- Password: pin to access the web server
High Availability
- Shutdown when inactive: defaults to false.
Options
| ID | Default | Values | Description |
|---|---|---|---|
| startupevents | false | true | generate IO events also during the driver’s start-up phase |
| false | start generating events only after HSYCO is aligned with the current status of the system | ||
| pollinterval | 1000 | n > 1000 | the data acquisition interval, in milliseconds |
| logsize | 300 | n ≥ 0 | the number of log lines to display in the UI object |
| gui | true | true | enable the UISET "visible" field for all partition zones |
| false | disable the UISET "visible" field for all partition zones | ||
| maxpartitions | 3 | 1≤n≤30 | number of partitions that are configured in the security panel |
Datapoints
| ID | Value | R/W | Description |
|---|---|---|---|
| connection | online | R | connection established |
| offline | R | HSYCO can't connect to the panel | |
| armed | 1 | W | arm all partitions in the system |
| 0 | W | disarm all partitions in the system | |
| p<n>.desc | <text> | R | description of partition <n> |
| p<n>.armed | 0 | R | partition <n> is disarmed |
| W | disarm partition <n> | ||
| 1 | R | partition <n> is armed | |
| W | arm partition <n> | ||
| p<n>.alarm | 0 | R | partition <n> not in alarm |
| 1 | R | partition <n> in alarm | |
| mem | R | partition <n> in alarm memory state | |
| p<n>.tamper | 0 | R | partition <n> not in tamper |
| 1 | R | partition <n> in tamper | |
| mem | R | partition <n> in tamper memory state | |
| z<n>.desc | <text> | R | description of zone <n> |
| z<n>.alarm | 0 | R | zone <n> not in alarm |
| 1 | R | zone <n> in alarm | |
| z<n>.mask | 0 | R | zone <n> not masked |
| 1 | R | zone <n> masked | |
| z<n>.tamper | 0 | R | zone <n> not in tamper |
| 1 | R | zone <n> in tamper | |
| z<n>.error | 0 | R | zone <n> not in error |
| 1 | R | zone <n> in error | |
| z<n>.bypass | 0 | R | zone <n> is not bypassed |
| W | unbypass zone <n> | ||
| 1 | R | zone <n> is bypassed | |
| W | bypass zone <n> | ||
| o<n>.desc | <text> | R | description of output <n> |
| o<n> | 0 | R | output <n> is off |
| W | turn off output <n> | ||
| 1 | R | output n <n> is on | |
| W | turn on output <n> | ||
| voltage.low | 0 | R | system voltage is ok |
| 1 | R | system voltage is low | |
| batt.low | 0 | R | battery is ok |
| 1 | R | battery is low | |
| batt.fault | 0 | R | battery is ok |
| 1 | R | battery fault | |
| pstn.fault | 0 | R | pstn is ok |
| 1 | R | pstn fault | |
| credit.low | 0 | R | credit is ok |
| 1 | R | credit is low | |
| system.fault | 0 | R | system is ok |
| 1 | R | system fault | |
| mobile.fault | 0 | R | mobile is ok |
| 1 | R | mobile fault | |
| s<n>.desc | <text> | R | description of scenario <n> |
| s<n> | 1 | W | trigger scenario <n> |
User Interface
Lares4 Object
The user interface for the Lares4 multi-area intrusion detection system:
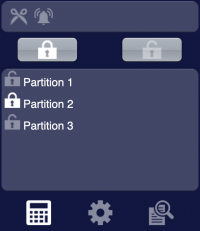
The first image shows the list of configured partitions. You can set the alarm for all the partitions, otherwise you can open a popup on a dedicated partition and set the alarm only for that one. The two icons on the top of the page represent in order: partition tamper (at least one partition is in tamper state), partition alarm (at least one partition is in alarm state).
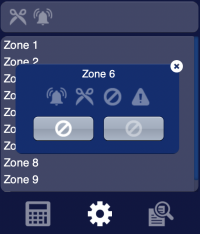
The second image shows the popup associated to a zone; the four icons shown inside the popup represent in order: zone alarm, zone tamper, zone bypassed, zone fault. Inside the popup you can bypass/unbypass the selected zone.
The (lares4) object is listed in the Project Editor’s new object list only when at least one Lares4 I/O Server is defined
Parameters
- server id: the server ID. Supports Redirect variables
- position: the object's position. Use the pixels or rows and columns coordinates format
Syntax
(lares4 <server id>; <position>)
E.g.
(lares4 lares; x10y20)
UISET Actions
| ID | Attribute | Set to | |
|---|---|---|---|
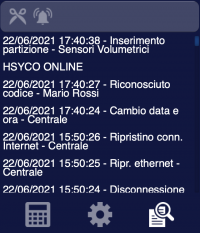
| log | value | latest security log lines (as many as specified by the 'logsize' option) | |
| log0 | value | latest security log (it will vanish after 5 seconds) | |
| z<n>.tamper | visible | false | zone n not in tampering |
| true | zone n in tampering | ||
| z<n>.bypass | visible | false | zone n not bypassed |
| true | zone n bypassed | ||
| z<n>.alarm | visible | false | zone n not in alarm |
| true | zone n in alarm | ||
| z<n>.error | visible | false | zone n not in error state |
| true | zone n in error state | ||
| z<n>.mask | visible | false | zone n not masked |
| true | zone n masked | ||
Log Files
If a Ksenia anti-intrusion unit is connected to HSYCO, the security.log file will be written in the same directories as the daily log files.
This file is never overwritten or deleted from HSYCO SERVER.
2018.02.20 16:59:28.516 - lares - 20/02/2018 16:56:36 - Disinserimento - Part 1 - U1 2018.02.20 17:00:24.527 - lares - 20/02/2018 16:57:36 - Inserimento - Part 1 - U1 2018.02.20 17:00:44.318 - lares - 20/02/2018 16:57:57 - Allarme - Zone 1 2018.02.20 17:00:49.241 - lares - 20/02/2018 16:57:58 - Ripristino - Zone 1 2018.02.20 17:00:54.043 - lares - 20/02/2018 16:58:06 - Disinserimento - Part 1 - U1 2018.02.20 17:01:18.905 - lares - 20/02/2018 16:58:29 - Fallita Comunicazione - Leonardo - Vocale GSM 2018.02.20 17:01:29.053 - lares - 20/02/2018 16:58:40 - Fallita Comunicazione - Leonardo - SMS
Other information about the Ksenia driver are stored in the message.log daily file.
Release Notes
3.8.0
- initial version release
Ksenia is a registered trademark of Ksenia Security s.r.l.